basic boilerplate + all the blog posts as of may 15
This commit is contained in:
commit
b13c7793f8
26 changed files with 1033 additions and 0 deletions
16
config.toml
Normal file
16
config.toml
Normal file
|
|
@ -0,0 +1,16 @@
|
|||
# The URL the site will be built for
|
||||
base_url = "https://fzorb.xyz"
|
||||
|
||||
# Whether to automatically compile all Sass files in the sass directory
|
||||
compile_sass = true
|
||||
|
||||
# Whether to build a search index to be used later on by a JavaScript library
|
||||
build_search_index = false
|
||||
|
||||
[markdown]
|
||||
# Whether to do syntax highlighting
|
||||
# Theme can be customised by setting the `highlight_theme` variable to a theme supported by Zola
|
||||
highlight_code = false
|
||||
|
||||
[extra]
|
||||
# Put all your custom variables here
|
||||
9
content/posts/08-10-2024-incident.md
Normal file
9
content/posts/08-10-2024-incident.md
Normal file
|
|
@ -0,0 +1,9 @@
|
|||
+++
|
||||
title = '08.10.2024 Incident'
|
||||
date = 2024-10-08T23:16:52+03:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
At around 16:09 GMT+3, fzorb.xyz and all its associated services went down. I wasn't able to investigate, as I was busy with other stuff until 19:05 GMT+3. It turns out that our VPS provider, Frantech/BuyVM, had a problem regarding their Router. Apparently, some guy at the datacenter Frantech colocates at left an USB stick in a router, so after a restart, it booted into the Junos install interface. Service has been restored ~30 minutes from the time of writing this.
|
||||
|
||||
There isn't really much to say about it. I'm sorry for the downtime.
|
||||
13
content/posts/1-12-2024-updates.md
Normal file
13
content/posts/1-12-2024-updates.md
Normal file
|
|
@ -0,0 +1,13 @@
|
|||
+++
|
||||
title = "01/12/2024 updates (& something about Romania's national day)"
|
||||
date = 2024-12-01T10:41:09+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
## Site updates
|
||||
* Yesterday I have moved the site to a new host, kinda. This is more of an "experiment" as to test how great my new VPS offer would handle a low traffic website.
|
||||
* I bit the forbidden apple (JavaScript) and you can now choose a theme for this website. Direct your attention the bottom of the page.
|
||||
* The Guestbook is back. Yay! Now using Isso.
|
||||
* Removed the Thoughts section.
|
||||
|
||||
Also I must now mention that today is a very special day in Romania. 106 years ago, 100.000 people went to Alba Iulia to sign the Declaration of Alba Iulia, and with that, Romania united with Transylvania, 318 years after their last separation.
|
||||
18
content/posts/128mb.md
Normal file
18
content/posts/128mb.md
Normal file
|
|
@ -0,0 +1,18 @@
|
|||
+++
|
||||
title = 'Using a 128MB NAT OpenVZ VPS'
|
||||
date = 2024-10-21T22:27:28+03:00
|
||||
draft = false
|
||||
+++
|
||||
While at a metro station, I was chatting with some friends on a Telegram group, when one of them shared an intriguing hosting provider: **Gullo's Hosting**. I couldn't believe my eyes when I saw a 3,50EUR/YR VPS, so I impulsively bought it. Now, it does have some caveats, such as:
|
||||
* Low storage space: I kept bashing my head against the wall trying to figure out how I could clear space.
|
||||
* No public IPv4: It's fine for a 3.50/yr VPS.
|
||||
|
||||
However you can't really complain for such a low price, so I just started setting some stuff up. The first thing I've thought of using this box for is a VPN. I tried getting Wireguard running, but I failed spectacularly.
|
||||
|
||||
On my first attempt I was quite hopeful, until I hit the storage limit when installing some dependencies Wireguard needed. So I just reset it. On the second attempt, I tried using Debian 11, maybe it uses less storage, but I started having problems installing dependencies.
|
||||
|
||||
In the end, I dropped the VPN idea and made a SOCKS5 proxy using `microsocks`. Setting it up was a breeze, however I wasn't able to find any no-bullshit tutorials on setting one up. Maybe one day I'll make a site in the vein of https://landchad.net/. Who knows?
|
||||
|
||||
And I would also like to add how annoying it is to use the console feature of Gullo. The password to the user created to access your container via SSH resets every few hours and it's very annoying to have to log into the panel every time I want to tweak something. I can probably setup SSH on my own container though, but I'll do it in the near future.
|
||||
|
||||
Anyways, it's getting late and I'm going to go to sleep. Thanks for reading.
|
||||
3
content/posts/_index.md
Normal file
3
content/posts/_index.md
Normal file
|
|
@ -0,0 +1,3 @@
|
|||
---
|
||||
---
|
||||
[<- return to index](/)
|
||||
35
content/posts/a-trip-to-the-CFR-museum.md
Normal file
35
content/posts/a-trip-to-the-CFR-museum.md
Normal file
|
|
@ -0,0 +1,35 @@
|
|||
+++
|
||||
title = 'A Trip to the CFR Museum'
|
||||
date = 2024-01-26T20:02:16+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
I've had the chance these past days to go to the CFR museum in Bucharest, Romania, where they had a beautiful train model, as well as many other things, such as a whole steam locomotive in their frontyard. I highly suggest anyone visits this museum. It may not be as big but it makes up in quality. It's next to the North Railway Station and is served by STB routes 1, 10, 82, 97, 105, 182, 282, as well as the Gara De Nord 2 (M4) Metro Station (Also Gara De Nord station. If you want to go to GDN2, you'll have to switch at Basarab).
|
||||
|
||||

|
||||
*A huge steam locomotive parked outside of the CFR museum*
|
||||
|
||||

|
||||
*A scaled down design of a cargo terminal*
|
||||
|
||||

|
||||
*Model of 060-EA-042 locomotive*
|
||||
|
||||

|
||||
*Model of LDH diesel locomotive*
|
||||
|
||||
## The model
|
||||

|
||||
*Doutchebahn locomotive hauling passenger cars*
|
||||

|
||||
*Siemens Desiro train*
|
||||

|
||||

|
||||
*Pictures of the train model*
|
||||

|
||||
*LDH in action*
|
||||

|
||||
*Depot*
|
||||
|
||||
|
||||
I hope these pictures can be of some use.
|
||||
14
content/posts/alpine.md
Normal file
14
content/posts/alpine.md
Normal file
|
|
@ -0,0 +1,14 @@
|
|||
---
|
||||
title: 'Installing Alpine Linux on an OpenVZ VPS'
|
||||
date: 2025-01-16T10:27:28+03:00
|
||||
draft: false
|
||||
---
|
||||
|
||||
A few months ago I talked about Gullo's hosting, a dirt cheap NAT VPS host that uses OpenVZ. I decided to put the two boxes I bought from them to work by running Yggdrasil nodes. However, I realised that modern Debian just doesn't really run too well on 128mb of ram. As such, I started looking for alternatives, but Gullo only supported Debian, CentOS and Ubuntu! Surely there must be a way to install Alpine, right?
|
||||
## Yes there is
|
||||
Using [this simple script](https://gist.github.com/pexcn/dc3ebe60393cc4ede40b30e180d40ac5) you can convert any OpenVZ-based VPS to a little Alpine box.
|
||||
## Using the script
|
||||
Using this script is trivially easy. All you must do is download the script and run it as root. Here's a one-liner that does it: `curl https://gist.github.com/pexcn/dc3ebe60393cc4ede40b30e180d40ac5/raw/8c2439d5d583dd40d5af3e570949b9f0974357ba/alpine.sh | sh`
|
||||
Note that this will erase EVERYTHING from your VPS!
|
||||
## Conclusion
|
||||
The script I showed you today is a really handy one, but I still yearn for the day Gullos will support Alpine out of the box.
|
||||
25
content/posts/altsom-coardia-stream.md
Normal file
25
content/posts/altsom-coardia-stream.md
Normal file
|
|
@ -0,0 +1,25 @@
|
|||
---
|
||||
title: 'The Altsom Coardia Stream and what it means for CFR'
|
||||
date: 2023-12-20T21:29:27+02:00
|
||||
draft: false
|
||||
---
|
||||
The first Class 101 trains from Altsom have arrived recently in Romania, and I have to say I am 3 weeks late to the party. I can't explain in words how big this is. This is CFR's first aquisition of new electric trains in 20 years. Below is a picture with the most common electric locomotives in Romania, the class 4x ones.
|
||||

|
||||
*A class 40 train of CFR Calatori at Bacau. Picture courtesy of Calin Strimbu.*
|
||||
|
||||
|
||||
These look like they belong in a scrap yard, don't they? A few years ago my parents were shocked at how old the locomotives were and they say that "they looked like they were 100 years old" and I don't blame them. We even have nearly 80 year old locomotives still in service. I'm not joking. Class 77 trains were produced from 1935 to 1942 and they still USE THEM, though it's for short routes.
|
||||

|
||||
*A class 77 train of CFR Calatori at Calimanesti station. Picture courtesy of Stefan Puscasu.*
|
||||
|
||||
|
||||
And here are the second newest trains of CFR calatori. Siemens Desiro, AKA Class 96
|
||||

|
||||
*A graffitied class 96 train of CFR Calatori at Bucuresti Nord. Picture courtesy of Stefan Puscasu.*
|
||||
|
||||
|
||||
And here we have the new Altsom trains.
|
||||

|
||||
*A brand new Altsom Coardia Stream train with a bit of snow. Picture courtesy of Observatorul Prahova*
|
||||
|
||||
Ever since the 2000s, CFR has started gaining the reputation of being **extremely** unreliable, with CFR having delays of **4 million minutes** ([source](https://www.digi24.ro/stiri/actualitate/calatorii-in-timp-la-cfr-trenurile-din-romania-au-intarziat-anul-trecut-cumulat-mai-bine-de-8-ani-2560019)) in 2022. Yikes. I don't know if the reason for these delays are rolling-stock related, but I have to say, I hope that's the case. I also don't even want to touch on the bathrooms of the passenger cars. Thank God I never had to take a number two in one of these, cause otherwise, I would've gotten all of the possible and impossible STDs. I won't show pictures, it's gross as hell, but if you are interested, google "veceu cfr". I am also interested in seeing if it will take less time to get there, as these trains can reach 200km/h, but we have horrible infrastructure. I hope the lines get modernized faster, so I can finally go to the beach in a decent timeframe.
|
||||
11
content/posts/animal-farm.md
Normal file
11
content/posts/animal-farm.md
Normal file
|
|
@ -0,0 +1,11 @@
|
|||
+++
|
||||
title = 'Thoughts on Animal Farm'
|
||||
date = 2025-04-28T20:51:19+03:00
|
||||
draft = true
|
||||
+++
|
||||
|
||||
Yesterday I've finished reading Animal Farm, and personally I believe that it is not only a parody of the Soviet Union - but also a parody of the current world.
|
||||
|
||||
By the way, this DOES contain spoilers, if you want to read it you might want to refrain from reading this article until you are done. While it may not be as popular as Orwell's "1984", I still think it deserves a read. If you enjoyed 1984, then you will enjoy this book too, as it explores many of the same themes as the aformentioned book.
|
||||
|
||||
For a quick summary: an old pig called Major has a dream he shared with his fellow animals: a dream where all animals are equal, a dream where humans, especially Mr Jones, the farm's owner, don't take their produce. While Old Major dies a few days later, his fellow animals were inspired by his message. Eventually, they have a revolution to kick the owner out of his farm. After that event, they change the farm's name from Manor Farm to Animal Farm. Two pigs step up to be the leaders of their new nation: Snowball and Napoleon.
|
||||
66
content/posts/ddwrt-as-a-wireless-client-bridge.md
Normal file
66
content/posts/ddwrt-as-a-wireless-client-bridge.md
Normal file
|
|
@ -0,0 +1,66 @@
|
|||
+++
|
||||
title = 'DD-WRT as a Wireless Client Bridge'
|
||||
date = 2024-09-16T18:55:11+03:00
|
||||
draft = false
|
||||
+++
|
||||
If you live in a house where extending a simple networking cable would require a lot of work, you might find yourself buying something like a network printer and not being able to connect it to the network due to it not supporting wifi. These situations suck, but thankfully, there's a solution, the Wireless Client Bridge.
|
||||
|
||||
## Okay, what the hell is that?
|
||||
A Wireless Client Bridge is a device that helps your computer/laptop/smart fridge connect to the internet when a direct wired connection to your main router wouldn't be possible.
|
||||
|
||||
### Pros:
|
||||
* No need to spend ages googling your wifi drivers
|
||||
* Better connections, as most commercial routers have better antennas than most commercial computers.
|
||||
|
||||
### Cons:
|
||||
* It's another appliance that you need to maintain and power.
|
||||
|
||||
Here's a handy diagram of what we'll be doing today:
|
||||

|
||||
|
||||
## 1. Setting up DD-WRT
|
||||
It should be obvious that you must install DD-WRT on a compatible router. I decided for this setup to go with the old but reliable TP-LINK TL-WR1043ND. But you may be asking yourself, why use DD-WRT? Well, DD-WRT is simpler than alternatives like OpenWRT. That's it.
|
||||
|
||||
## 2. Initial setup
|
||||
After flashing DD-WRT, you should go to the setup tab, and fill in the following:
|
||||
* **Connection Type**: Disabled
|
||||
* **Router Name**: Can be changed to anything
|
||||
* **Local IP Address**: You need to select an IP address that is not already in use on your network. For example, I chose 192.168.1.2. If your network uses a different address range, such as 192.168.0.x or 10.10.1.x, you'll need to pick an IP from that range, like 192.168.0.2 or 10.10.1.2.
|
||||
* **Gateway**: You must input the IP of your main router
|
||||
* **Assign WAN Port to Switch**: Enable
|
||||
* **DHCP Server**: Disable
|
||||
|
||||
Your settings should look something like this
|
||||

|
||||
|
||||
## 3. Disabling the firewall
|
||||
This can be done via Security > Firewall
|
||||
* **SPI Firewall**: Disable
|
||||
|
||||
Now you may be thinking why you'd disable the firewall. Well, that is handled by your main router.
|
||||
|
||||

|
||||
|
||||
## 4. Connecting to the wireless network:
|
||||
Go to Wireless > Basic Settings and fill in the following:
|
||||
* **Wireless Mode**: Client Bridge (Routed)
|
||||
* **Default GW Mode**: Manual
|
||||
* **Gateway**: The IP of your main router. Mine's 192.168.1.1
|
||||
* **Wireless Network Mode**: Mixed
|
||||
* **Wireless Network Name (SSID)**: Your SSID. I redacted mine.
|
||||
|
||||

|
||||
|
||||
Now go to the Wireless Security tab and chose the following (these are the most common settings found on most routers):
|
||||
* **Security Mode**: WPA
|
||||
* **Network Authentication**: WPA2 Personal
|
||||
* **WPA Shared Key**: your password
|
||||
|
||||

|
||||
|
||||
Now you can check if you configured the wireless stuff correctly by going to the Status > Wireless tab and reviewing the stuff there.
|
||||
|
||||
## 5. Profit
|
||||
Now you can finally apply all the changes. You'll have to change to 192.168.1.2 or whatever IP you chose in step 1 for the router.
|
||||
|
||||
I am still a DD-WRT novice, so if I missed anything, or something doesn't work properly, please let me know.
|
||||
12
content/posts/fzorb-dot-xyz-updates-christmas-edition.md
Normal file
12
content/posts/fzorb-dot-xyz-updates-christmas-edition.md
Normal file
|
|
@ -0,0 +1,12 @@
|
|||
+++
|
||||
title = 'fzorb.xyz Updates: Christmas Edition'
|
||||
date = 2024-12-25T10:08:47+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Merry Christmas! These past few days I have done the following changes:
|
||||
* `xmin` is now the default theme. I consider it to look better. You can choose the old `red` theme at the bottom of the page.
|
||||
* Overhauled the site a little. Mainly made the index page less... flashy.
|
||||
* E-Mail is back online.
|
||||
* There is now a [webring](/webring)! [Contact me](/contact) to get added.
|
||||
* There is now a [song of the now](/sotn)! The current SOTN gets displayed on the index page.
|
||||
90
content/posts/honeypot.md
Normal file
90
content/posts/honeypot.md
Normal file
|
|
@ -0,0 +1,90 @@
|
|||
+++
|
||||
title = 'Running an SSH honeypot to troll skids'
|
||||
date = 2025-01-03T11:10:19+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
If you've ever looked at a public server's SSH logs, you would have probably found tens of failed connections from IP addresses you are not associated with. Those are bots that are trying to bruteforce their way into your Linux bots. An easy way you can change this is by changing the SSH port, but that's just lame. What you should do is do a *little bit of trolling*. So today, we'll be configuring `sshesame` to listen on port 22 and some other common ssh ports.
|
||||
|
||||
## Prerequisites
|
||||
* A public Linux server running a *nix distribution
|
||||
* Some moderate CLI experience
|
||||
* Patience
|
||||
|
||||
## Obtaining the binaries
|
||||
If you're using Debian, like me, you can easily install sshesame, as [there is a package for it](https://packages.debian.org/bookworm/sshesame) (that apparently is terribly out of date but it is fine enough), but on other distributions, you might have to follow other instructions. Other distros might have to compile it from source, which I was going to do anyway.
|
||||
|
||||
```sh
|
||||
git clone https://github.com/jaksi/sshesame
|
||||
cd sshesame
|
||||
go build
|
||||
mv sshesame /usr/local/bin # You don't have to use this path if you don't want to
|
||||
```
|
||||
|
||||
## Moving SSH from port 22
|
||||
This can be easily done by editing `/etc/ssh/sshd_config`. Uncomment the 14th line and replace 22 with any port you want. Personally, I use 69 because it's very funny number!!! Make sure to restart the `sshd` service after changing the port.
|
||||
|
||||
## Configuring sshesame
|
||||
Now that we've got sshesame, we can get to configuring it. For advanced users, you should probably edit the sample configuration file from [here](https://github.com/jaksi/sshesame/blob/master/sshesame.yaml), which contains a lot more options, but personally, I think most of the people reading my ramblings would get away with the basic configuration I will share below. Feel free to write the configuration wherever you want, but I prefer having it in /etc/sshesame.yaml
|
||||
|
||||
**sshesame.yaml**
|
||||
```yaml
|
||||
server:
|
||||
listen_address: 0.0.0.0:22
|
||||
host_keys: null
|
||||
|
||||
logging:
|
||||
file: null
|
||||
json: false
|
||||
timestamps: true
|
||||
debug: false
|
||||
metrics_address: null
|
||||
split_host_port: false
|
||||
|
||||
auth:
|
||||
no_auth: false
|
||||
max_tries: 0
|
||||
|
||||
password_auth:
|
||||
enabled: true
|
||||
accepted: true
|
||||
|
||||
public_key_auth:
|
||||
enabled: false
|
||||
accepted: false
|
||||
|
||||
ssh_proto:
|
||||
version: SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.2
|
||||
banner: Hewwo skids :3
|
||||
rekey_threshold: 0
|
||||
key_exchanges: null
|
||||
ciphers: null
|
||||
macs: null
|
||||
```
|
||||
|
||||
Now you can just execute `sshesame -config /etc/sshesame.yaml` and you will have a honeypot, but you probably want this to run whenever your system starts, for this we can use systemd.
|
||||
|
||||
## Sshesame as a Systemd service
|
||||
Create a new file, `/etc/systemd/system/sshesame.service`, and populate it with the following contents.
|
||||
```ini
|
||||
[Unit]
|
||||
Description=SSH honeypot
|
||||
After=network-online.target
|
||||
Wants=network-online.target
|
||||
|
||||
[Service]
|
||||
ExecStart=/usr/local/bin/sshesame -config /etc/sshesame.yaml
|
||||
Restart=always
|
||||
|
||||
[Install]
|
||||
WantedBy=multi-user.target
|
||||
```
|
||||
|
||||
```sh
|
||||
systemctl daemon-reload
|
||||
systemctl enable --now sshesame
|
||||
```
|
||||
|
||||
And now you can have skids waste their time hacking your box. Yay!
|
||||
|
||||
P.S. Happy 2025
|
||||
70
content/posts/how-not-to-use-cloudflare.md
Normal file
70
content/posts/how-not-to-use-cloudflare.md
Normal file
|
|
@ -0,0 +1,70 @@
|
|||
+++
|
||||
title = 'How Not to Use Cloudflare'
|
||||
date = 2024-04-02T18:20:15+03:00
|
||||
draft = false
|
||||
+++
|
||||
Cloudflare is a DDoS mitigation platform which offers free proxying of your origin server. Unfortunately, this proxying is not well-used by some people, such as the person who inspired me to make this blog post. He has since fixed it. On Sunday, me and a friend of mine have exposed a vulnerability to one of our other friends, which we will be referring for privacy reasons as X. X has agreed to the "hacking" of his website.
|
||||
|
||||
## What is Cloudflare proxying?
|
||||
In order to mitigate DDoS attacks, Cloudflare must proxy your website throught one of their many proxy servers. This means, Cloudflare accesses your website instead of your user. While this may be a privacy concern, we will not adress it as it is not the point of this document, instead, I direct you to https://0xacab.org/dCF/deCloudflare/-/blob/master/README.md.
|
||||
|
||||
## The issue
|
||||
The person configured his webserver incorectly, and instead of denying all of the requests from IPs that are not of Cloudflare (see https://cloudflare.com/ips/), it allows any traffic on port 80. Port 80 is the default web port for unencrypted traffic. The individual did not have an SSL certificate, instead relying on one provided by Cloudflare. This is not reccomended and was used as part of the attack vector.
|
||||
|
||||
Due to the fact that they allow all IPs to request port 80, if we have his origin IP, which was easily found via https://search.censys.io/, we could send a direct request to the server. Below is showing a direct request to my server, if we access it from the direct IP, without any host headers.
|
||||
|
||||
```
|
||||
> curl http://107.189.28.28
|
||||
<!DOCTYPE html>
|
||||
<html>
|
||||
<head>
|
||||
<title>Welcome to nginx!</title>
|
||||
<style>
|
||||
body {
|
||||
width: 35em;
|
||||
margin: 0 auto;
|
||||
font-family: Tahoma, Verdana, Arial, sans-serif;
|
||||
}
|
||||
</style>
|
||||
</head>
|
||||
<body>
|
||||
<h1>Welcome to nginx!</h1>
|
||||
<p>If you see this page, the nginx web server is successfully installed and
|
||||
working. Further configuration is required.</p>
|
||||
|
||||
<p>For online documentation and support please refer to
|
||||
<a href="http://nginx.org/">nginx.org</a>.<br/>
|
||||
Commercial support is available at
|
||||
<a href="http://nginx.com/">nginx.com</a>.</p>
|
||||
|
||||
<p><em>Thank you for using nginx.</em></p>
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
|
||||
This is the result of sending the same request but with the host header set to fzorb.xyz:
|
||||
|
||||
```
|
||||
>curl 107.189.28.28 --header "Host: fzorb.xyz"
|
||||
<html>
|
||||
<head><title>301 Moved Permanently</title></head>
|
||||
<body>
|
||||
<center><h1>301 Moved Permanently</h1></center>
|
||||
<hr><center>nginx/1.18.0</center>
|
||||
</body>
|
||||
</html>
|
||||
```
|
||||
This is the response you get if you try going to http://fzorb.xyz/. It redirects you to the secure version, https://fzorb.xyz/.
|
||||
|
||||
## But why would you want to bypass the origin?
|
||||
We had more "humble" motive. The website in question checked your IP address before accessing the website so it wouldn't be from a certain country to join a Discord guild in order to prevent someone from joining. I found this absurd so I came up with the attack vector, and my friend did the actual exploiting of this vulnerability. This was used to prevent geoblocking. But this could also be used in worse ways, such as impersonating admins on a forum for example. In fact, Stack Overflow in its early days determined admins by their IP address, which in this case was 127.0.0.1. This is not secure at all.
|
||||
|
||||
## So how does this work?
|
||||
The webserver knows your IP address via a header called X-Forwarded-For. Cloudflare doesn't use that header, instead using CF-Connecting-IP. In the absence of Cloudflare, you can set CF-Connecting-IP to any value you want and the Webserver will think it is valid. You could set your ip to values like `1.1.1.1`, `1.3.3.7`, `69.69.69.69`, or maybe even `420.420.420.420`, and the webserver can't know any better.
|
||||
|
||||
## How do I mitigate it?
|
||||
You can mitigate it via numerous ways. Here are the 2 ways you can do that:
|
||||
* Disable Cloudflare proxying: this is the option X chose. This may not be an option for you though if you are subject to frequent (D)DOS attacks.
|
||||
* Deny access of all Cloudflare IPs: there is a handy script on Github made by user Icseon, which uses iptables to deny all non-Cloudflare traffic on port 80 and 443. https://github.com/icseon/cf-iptables
|
||||
|
||||
I hope this blog post has been useful. While I do not use Cloudflare myself, I know many people that do.
|
||||
20
content/posts/ipv6-adventures.md
Normal file
20
content/posts/ipv6-adventures.md
Normal file
|
|
@ -0,0 +1,20 @@
|
|||
+++
|
||||
title = 'IPv6 Adventures'
|
||||
date = 2024-10-23T09:27:29+03:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Today's story starts in a similar vein as to the last one. While waiting for a train, I stumbled across a provider which offered extremely cheap hosting, and severely undercut Gullo. Their name is [C-SERVERS](https://c-servers.co.uk/) and they seem to be reselling Hetzner, just like Gullo, but they give you more ram, at the cost of not giving you any IPv4 ports, at least as far as I can tell. So I bought one of their NanoVPS servers. Then, I hit my first roadblock... I can't SSH!
|
||||
Unfortunately, due to my ISP being stupid, enabling IPv6 on our home router would do more harm than good, so as a temporary measure, I decided to use [tunnelbroker](https://tunnelbroker.net), which gave me a free IPv6 address. And now I can SSH!
|
||||
|
||||
After I got in, I decided that I can host a Discord bot for some of my friends, since that doesn't require a public IP. Yes yes I know what you're going to say "b-but don't you hate discord??" yes I do but unfortunately 70% of my friends aren't smart enough to use IRC or any alternative.
|
||||
|
||||
My prefered mode of deployment is Docker, but then I hit my second roadblock... I can't update!
|
||||
|
||||
Debian's repositories have IPv6 support, and the VPS came with NAT64, but apparently, the ruby image I wanted to use, which is based on Debian, couldn't update. I bashed my head against the wall trying to figure out how I could update it, but I gave up running it in Docker. So I decided to do it the old fashioned way. I setup an user, and then when I was getting an up to date copy of my bot's source code from my git server, I hit my third roadblock: I can't clone!
|
||||
|
||||
Looks like I didn't have IPv6 enabled on the VPS hosting my git forge. Oops! It didn't take long to setup, but now I can rest easy at night knowing IPv6 chads can access my site directly.
|
||||
|
||||
After a bit of tinkering with rbenv and making a swapfile, I finally got Ruby rolling, and I finally got Jon back up and running! Yay!
|
||||
|
||||
I wouldn't say IPv6 is bad, it's the future, but I do consider it still got a long long long way to go. IPv4 isn't going anytime soon, but if you go on https://www.google.com/intl/en/ipv6/statistics.html, you'll see that IPv6 adoption is steadily growing, so you should probably stop putting off setting up IPv6. I encourage you to do so, [you'll be more up to date than Discord if you do that](https://support.discord.com/hc/en-us/community/posts/360047840052-Add-IPv6-support).
|
||||
69
content/posts/making-a-beta-1.7.3-server.md
Normal file
69
content/posts/making-a-beta-1.7.3-server.md
Normal file
|
|
@ -0,0 +1,69 @@
|
|||
+++
|
||||
title = 'Making a Beta 1.7.3 Server (with Docker)'
|
||||
date = 2025-03-06T20:00:46+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
You miss when Minecraft was simpler? Want to go back to a time before The Adventure Update released? Well, look no further than this guide. I will be guiding you thorugh the entire setup process of a Minecraft Beta 1.7.3 server, with some basic plugins and we'll also be running the server through Docker. So make yourself comfortable and without any further ado, let's begin!
|
||||
|
||||
## Prerequisites
|
||||
* Some sort of Linux server:
|
||||
* **A VPS**: There isn't really that much need for huge ammounts of ram, and as such you can probably go with the cheapest host you can find on LowEndTalk which gives you around a gigabyte of ram. Remember, we aren't running a Minecraft server for the latest version, so we can cheap out on RAM. Fun fact: [for a while, MinecraftOnline, the world's oldest Minecraft server, was being run on a box with 1.5GB of RAM!](https://minecraftonline.com/wiki/Hardware#Hemingway). You could also try your luck with a NAT VPS, if you don't mind not having the default port (25565) available.
|
||||
* **A physical server**: You can probably run this entire setup on an almost 20 year old C2D computer and have acceptable performance. A con would be that you need to port forward, which is getting less and less common as ISPs are implementing CGNAT. If you have CGNAT, you won't be able to port forward. A workaround would be reverse proxying the server, but NAT Masquerading would make it nearly impossible to get a Player's real IP, unless someone implements the [PROXY protocol](https://seriousben.com/posts/2020-02-exploring-the-proxy-protocol/) in the old and obscure Craftbukkit build we're going to be using. Though Playit, a popular tunneling/reverse proxying service, maps every source IP to a random IPv4 127.0.0.0/8 range.
|
||||
* **Shared hosting**: Just get something decent. I've had a pleasant experience with [WitherHosting](https://witherhosting.com/) a few years ago, but I can't really vouch. Look around and find something decent.
|
||||
* Some Linux knowledge
|
||||
* Docker
|
||||
* (optional) Some networking knowledge
|
||||
* (optional) Java 8 - you can skip over this if you decide to just use Docker.
|
||||
|
||||
## Getting started.
|
||||
To run a Minecraft server, you must get a server JAR. We will be using Craftbukkit CB1060, which seems to be a community favorite when it comes to beta 1.7.3 servers. Archive.org hosts a CB1060 build which you can download. But first we'll make a directory.
|
||||
```
|
||||
mkdir /srv/minecraft
|
||||
cd /srv/minecraft
|
||||
curl https://archive.org/download/craftbukkit1060/craftbukkit1-7-3%281060%29.jar -o craftbukkit.jar
|
||||
#and now let's generate the skeleton!
|
||||
java -Xmx1G -jar craftbukkit.jar
|
||||
```
|
||||
|
||||
Alright, now we've generated the server files, click CTRL+C or enter the `stop` command to stop the server. We can't join the server yet! We have to disable authentication and download the AuthMe plugin!
|
||||
|
||||
```
|
||||
curl https://mediafilez.forgecdn.net/files/540/724/AuthMe-2.0.jar -o plugins/AuthMe.jar
|
||||
```
|
||||
Installing AuthMe is as simple as that! You can enable sessions within `plugins/AuthMe/config.yml`, which will make it so users don't have to log in again if they've already logged in from that IP in a reasonable timeframe. However, **this is a huge sequrity risk if you have to resort to tunneling services, beware!!!**
|
||||
|
||||
Okay, now to disable authentication, we'll have to edit the `server.properties` file, more specifically line 7, set `online-mode` to false. We can now start the server again via `java -Xmx1G -jar craftbukkit.jar`.
|
||||
|
||||
Now hop on, register with a strong password, and give your account operator status via the `op` command.
|
||||
|
||||
## Docker time!
|
||||
Firstly, it is a wise idea to move everything in your `/srv/minecraft` server to a `data/` folder, now you may be wondering why I am only using Docker after making the server on bare metal. Well, it's easier to setup a base Minecraft server this way. Okay, enough talking.
|
||||
```
|
||||
mkdir data
|
||||
mv ./* ./data #ignore whatever error you get, the operation would happen anyways
|
||||
nano Dockerfile compose.yml
|
||||
```
|
||||
|
||||
**Dockerfile**
|
||||
```
|
||||
FROM eclipse-temurin:8-jre-alpine
|
||||
WORKDIR /data
|
||||
CMD java -Xmx1G -jar ./craftbukkit.jar
|
||||
```
|
||||
|
||||
**compose.yml**
|
||||
```
|
||||
services:
|
||||
minecraft:
|
||||
build: .
|
||||
container_name: minecraft
|
||||
ports:
|
||||
- "25565:25565"
|
||||
volumes:
|
||||
- "./data:/data"
|
||||
restart: always
|
||||
```
|
||||
|
||||
## Now it's time to expose your server to the internet!
|
||||
You can simply port forward your server via your router, however if you don't have a dedicated IPv4 address you must use a proxy. See [my proxying guide](https://fzorb.xyz/posts/safely-selfhosting/) if you want to setup your own reverse proxy, or you can just use Playit.
|
||||
19
content/posts/march-updates.md
Normal file
19
content/posts/march-updates.md
Normal file
|
|
@ -0,0 +1,19 @@
|
|||
+++
|
||||
title = 'March Updates'
|
||||
date = 2025-03-06T07:01:01+02:00
|
||||
draft = false
|
||||
+++
|
||||
Okay, I have dissapeared for about two months, sorry about that. I just didn't really have something interesting to write about. In the meantime, I overhauled the website. Here are the details:
|
||||
* **No more JavaScript** - it was optional anyways
|
||||
* **Guestbook and themes are no more** - the first one was starting to get abused and was nothing but a collection of the most stupid things I have seen on the internet, second was extremely pointles
|
||||
* **New theme** - looks pretty neat, index page idea shamelessly stolen from https://denshi.org
|
||||
* **Most of the services are no longer around** - only exceptions being the 4get server (although broken #willfixeventually) and in some way the git server. I've decided to use Gitlab instead of Gitea because it has better CI/CD in my humble opinion (as well as more documentation). The new git server is https://code.be4.pw/ -- shoot me an email if you create an account on there, as I seldomly look at the accounts waiting approval.
|
||||
|
||||
Most things I wanted to do in the next four months (see [/projects#ideas](/projects/#ideas)) have been unfortunately postponed due to exams. Unless I get something interesting to write about, I don't think I'll make a new blog post until the end of June, [no spoilers tho](https://whois.domaintools.com/fzorb.xyz).
|
||||
|
||||
As such, due to exams, it pains me to say this but this website will go unmaintained for a few months.
|
||||
|
||||
Take care,
|
||||
fzorb
|
||||
|
||||
|
||||
81
content/posts/microsocks-on-netbsd.md
Normal file
81
content/posts/microsocks-on-netbsd.md
Normal file
|
|
@ -0,0 +1,81 @@
|
|||
+++
|
||||
title = 'Microsocks on NetBSD'
|
||||
date = 2024-10-28T07:44:51+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Have you ever wanted a proxy server that you can run on a toaster (literally)? Well, enter today's setup, Microsocks on NetBSD. Microsocks is a simple, fast and efficient SOCKS5 server. NetBSD is a highly portable UNIX system that you can literally run on a toaster.
|
||||
<p align="center">
|
||||
<img src="/pictures/netbsd-toaster.jpeg" />
|
||||
</p>
|
||||
|
||||
## Prerequisites
|
||||
* Something running NetBSD
|
||||
* Internet connection
|
||||
|
||||
## Getting microsocks
|
||||
Microsocks is not in the NetBSD repositories as far as i can tell, so we'll just compile it.
|
||||
```
|
||||
git clone https://github.com/rofl0r/microsocks
|
||||
cd microsocks
|
||||
make
|
||||
make install
|
||||
```
|
||||
And now we have installed Microsocks. Yay! You could just run it in a `screen` or something, but that's not very practical and actually pretty lame, so we'll setup an rc script.
|
||||
|
||||
## Setting up the rc script
|
||||
Firstly, open /etc/rc.d/microsocks with your preferred editor (I use `Vim` BTW) and add the script below
|
||||
```sh
|
||||
#!/bin/sh
|
||||
#
|
||||
# PROVIDE: microsocks
|
||||
# REQUIRE: DAEMON
|
||||
|
||||
. /etc/rc.subr
|
||||
|
||||
name="microsocks"
|
||||
rcvar=$name
|
||||
command="/usr/local/bin/microsocks"
|
||||
pidfile="/var/run/${name}.pid"
|
||||
start_cmd="microsocks_start"
|
||||
stop_cmd="microsocks_stop"
|
||||
|
||||
microsocks_start() {
|
||||
if [ -f "$pidfile" ] && kill -0 $(cat "$pidfile") 2>/dev/null; then
|
||||
echo "$name is already running."
|
||||
else
|
||||
echo "Starting $name..."
|
||||
${command} &
|
||||
echo $! > "$pidfile"
|
||||
echo "$name started with PID $(cat "$pidfile")."
|
||||
fi
|
||||
}
|
||||
|
||||
microsocks_stop() {
|
||||
if [ -f "$pidfile" ]; then
|
||||
echo "Stopping $name..."
|
||||
kill -TERM $(cat "$pidfile") && rm -f "$pidfile"
|
||||
echo "$name stopped."
|
||||
else
|
||||
echo "$name is not running."
|
||||
fi
|
||||
}
|
||||
|
||||
load_rc_config $name
|
||||
run_rc_command "$1"
|
||||
```
|
||||
|
||||
Direct your attention towards line 10. There we have the command that starts Microsocks. It doesn't necesarrily need arguments, as such, we can leave it as such, but that's not reccomended. Consult [this page](https://github.com/rofl0r/microsocks/blob/master/README.md#command-line-options) for more information on what arguments you can use.
|
||||
|
||||
Now to test everything is working, you can use this command:
|
||||
```
|
||||
service microsocks onestart
|
||||
```
|
||||
If you're able to connect to your proxy, you've configured it properly. We can now enable it in `/etc/rc.conf`, where we'll append:
|
||||
```
|
||||
microsocks=YES
|
||||
```
|
||||
And now we can restart and you'll see that our proxy is still alive.
|
||||
|
||||
## Conclusion
|
||||
NetBSD is pretty cool.
|
||||
31
content/posts/my-servers-2023.md
Normal file
31
content/posts/my-servers-2023.md
Normal file
|
|
@ -0,0 +1,31 @@
|
|||
+++
|
||||
title = 'My Servers (2023 edition)'
|
||||
date = 2023-12-20T20:11:58+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Over the past 5 years, I have inherited my father's philosophy of self-hosting. It all started with my brand-new Raspberry Pi 4. I wanted to create a Minecraft Server for me and my friends to play on. Unfortunately, due to my lack of skill, I have had to offload the responsibility onto my father's server (which was really weak! an intel celeron j1800 was barely cutting it for versions newer than 1.12.2!). Eventually, during quarantine, my father had moved his entire suite of servers (mainly SBCs) to the j1800 and it was beginning to get quite horrible. We were lucky to even get 18 TPS when more than 2 people were on.
|
||||
|
||||
Eventually, I've decided that the j1800 wasn't good enough anymore, so I've decided to get an old laptop motherboard with an Intel Core 2 Duo. Due to me barely knowing shit, I was quite frankly hooking that poor laptop motherboard to a monitor and starting the Minecraft server in a new window, which wasn't and still isn't a good thing, as it required me to be at home, it wasn't an issue for spring 2020 though.. After 3 months of doing it this crappy way, my father spent an afternoon teaching me how to enable the sshd daemon and figuring out how to make the Minecraft server autostart. Eventually he convinced me to just use Docker, and I have to say, I **really** enjoyed it, so much so that until recently I **only** (with a few exceptions like nginx) used docker.
|
||||
|
||||
Nowadays, the only component that remained the same through all of these 3 years worth of administration was Docker. I have learnt a lot just during this year alone and my system adminsitration knowledge doubled compared to last year. The motive for this blog post is to reflect on my progress this year and what I have learnt.
|
||||
|
||||
# The components
|
||||
My suite of servers is comprised of the following few lads:
|
||||
* **Frantech/BuyVM** VPS:
|
||||
I use this as a VPN in order for me to be able to expose my services to the internet without needing to port forward on my home IP address.
|
||||
* **HP t620 Thin Client**
|
||||
This is the brains of the whole operation and I find it hilarious how last year I thought I'd be using a more beefy server, but this lad, which cost me 5 dollars by the way, went above and beyond for me. I strongly reccomend the HP t620 for hosting basic websites, fediverse instances and Minecraft servers (though you should use purpur or you will experience a lot of lag!).
|
||||
* **Raspberry Pi 4**
|
||||
I still use this guy for stuff that **must** only be accessed on my home network. Stuff like Bitwarden, althrough I also run a Jellyfin server meant for public use, by my friends of course.
|
||||
* **Wyse 3040**
|
||||
This lad is a new addition to my homelab. I run an experimental Terraria server on it.
|
||||
|
||||
# The stack
|
||||
For all critical services, I prefer to run them on bare metal, as to not depend on one too many daemons. As I was saying earlier in this blog post, I still use Docker after 3 years of non-stop use. Recently however, I have dabbled into some Proxmox shenanigans and for a while I was reconsidering my faith... until I saw how badly virtual machines performed on the t620. Arguably it isn't really a wise choice to run Proxmox on it and I've ultimately decided that I was better off with just Docker.
|
||||
|
||||
# My regrets
|
||||
I should have gotten more ram and I should've not had to rely on Wireless internet, which is a node which can fail within my setup. I should've used ethernet. Unfortunately, I cannot convince my father to help me extend an ethernet cable to my room.
|
||||
|
||||
# Conclusion
|
||||
I strongly enocourage self-hosting everything you can, as it helps fight decentralization and you can often times find it better to use free and open source alternatives to things such as Google Calendar or Gmail.
|
||||
22
content/posts/my-servers-2024.md
Normal file
22
content/posts/my-servers-2024.md
Normal file
|
|
@ -0,0 +1,22 @@
|
|||
+++
|
||||
title = 'My Servers (2024 edition)'
|
||||
date = 2024-09-10T06:30:27+03:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
About a year ago, I have made a blog post about how I run things round here. Since then, a lot of things have passed. Since I think that I'm more free now than I will be in 3 months, when I initally planned on making this post, I've decided to just do it now.
|
||||
|
||||
# The components
|
||||
My suite of servers is comprised of the following computers:
|
||||
* **Frantech/BuyVM** VPS:
|
||||
I use this as a VPN in order for me to be able to expose my services to the internet without needing to port forward on my home IP address. It also doubles as an email server, so that's neat.
|
||||
* **HP Elitedesk 800 G2 mini**
|
||||
This is the server that runs everything. I have installed Proxmox on it. I have a few VMs and containers.
|
||||
Since this computer comes in multiple variations, here are the specifications for the model I have:
|
||||
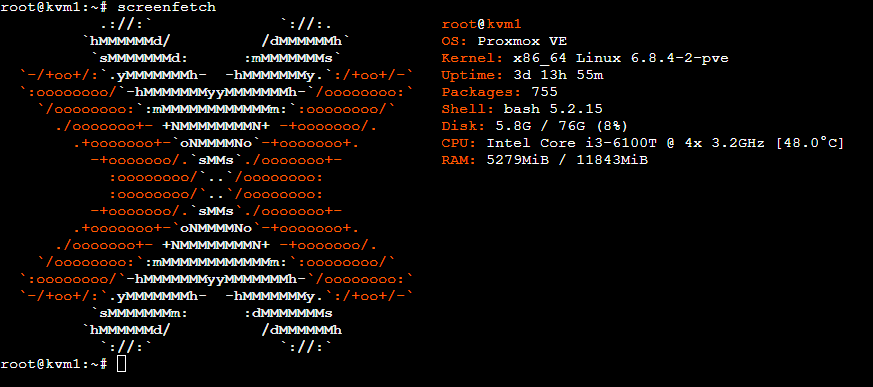
|
||||
|
||||
# The stack
|
||||
I primarily use docker for just about everything (minus the matrix server), as it is a pretty convenient way to spin up containers and not have to deal with houndreds of dependencies, or in some cases, convoluted installation procedures.
|
||||
|
||||
# My regrets
|
||||
I don't really have any regrets for my current setup, as everything is running fine, but in the future I wish to upgrade to 16gb of ram, and maybe a better CPU.
|
||||
112
content/posts/nitter.md
Normal file
112
content/posts/nitter.md
Normal file
|
|
@ -0,0 +1,112 @@
|
|||
+++
|
||||
title = 'Nitter in 2024'
|
||||
date = 2024-09-05T10:34:46+03:00
|
||||
draft = false
|
||||
+++
|
||||
Earlier this year, [Nitter has ceased development](https://github.com/zedeus/nitter/issues/1155#issuecomment-1913361757), due to the removal of guest accounts, but, you can still self host an alternative Twitter frontend, and we'll do it with something some love and some hate, Docker!
|
||||
|
||||
We will be using [Privacydevel's Nitter fork](https://github.com/PrivacyDevel/nitter) for this.
|
||||
|
||||
### Prerequisites:
|
||||
* A Linux server with Docker and Docker-compose installed
|
||||
* A few twitter accounts
|
||||
* A machine with a residential IP (for logging into your twitter alts, nothing else. You can use a smartphone for this)
|
||||
|
||||
### Step 1. Getting accounts
|
||||
For this you will need a residential IP, as the login script won't work otherwise. You can simply run it on your computer or on your phone using something like Termux.
|
||||
|
||||
After you get a bunch of alts, it is time to get their oauth tokens.
|
||||
```bash
|
||||
curl https://raw.githubusercontent.com/PrivacyDevel/nitter/master/twitter_oauth.sh -o twitter_oauth.sh
|
||||
vim twitter_oauth.sh
|
||||
```
|
||||
**twitter_oauth.sh**
|
||||
```sh
|
||||
...
|
||||
5 | username="yourUsernameHere"
|
||||
6 | password="yourPasswordHere"
|
||||
...
|
||||
```
|
||||
```sh
|
||||
bash twitter_oauth.sh
|
||||
```
|
||||
You'll end up with something similar in your terminal:
|
||||
```json
|
||||
{"oauth_token":"SECRET", "oauth_token_secret":"SECRET"}
|
||||
```
|
||||
Save it for later.
|
||||
|
||||
### Setting up Nitter
|
||||
```bash
|
||||
# Clone the instance. We will be using /srv/nitter
|
||||
$ git clone https://github.com/PrivacyDevel/nitter.git /srv/nitter
|
||||
# Now we have to edit the guest_accounts.json file
|
||||
$ vim guest_accounts.json
|
||||
```
|
||||
**guest_accounts.json**
|
||||
```json
|
||||
[{"oauth_token":"SECRET", "oauth_token_secret":"SECRET"}]
|
||||
```
|
||||
```bash
|
||||
# We'll also have to edit the docker-compose.yml file to pass the guest_accounts.json to the container.
|
||||
$ vim docker-compose.yml
|
||||
```
|
||||
```yaml
|
||||
version: "3"
|
||||
|
||||
services:
|
||||
|
||||
nitter:
|
||||
image: ghcr.io/privacydevel/nitter:master
|
||||
container_name: nitter
|
||||
ports:
|
||||
- "8080:8080" # Replace with "8080:8080" if you don't use a reverse proxy.
|
||||
volumes:
|
||||
- ./nitter.conf:/src/nitter.conf:Z,ro
|
||||
- ./guest_accounts.json:/src/guest_accounts.json:Z,ro
|
||||
depends_on:
|
||||
- nitter-redis
|
||||
restart: unless-stopped
|
||||
healthcheck:
|
||||
test: wget -nv --tries=1 --spider http://127.0.0.1:8080/Jack/status/20 || exit 1
|
||||
interval: 30s
|
||||
timeout: 5s
|
||||
retries: 2
|
||||
user: "998:998"
|
||||
read_only: true
|
||||
security_opt:
|
||||
- no-new-privileges:true
|
||||
cap_drop:
|
||||
- ALL
|
||||
|
||||
nitter-redis:
|
||||
image: redis:6-alpine
|
||||
container_name: nitter-redis
|
||||
command: redis-server --save 60 1 --loglevel warning
|
||||
volumes:
|
||||
- nitter-redis:/data
|
||||
restart: unless-stopped
|
||||
healthcheck:
|
||||
test: redis-cli ping
|
||||
interval: 30s
|
||||
timeout: 5s
|
||||
retries: 2
|
||||
user: "999:1000"
|
||||
read_only: true
|
||||
security_opt:
|
||||
- no-new-privileges:true
|
||||
cap_drop:
|
||||
- ALL
|
||||
|
||||
volumes:
|
||||
nitter-redis:
|
||||
|
||||
```
|
||||
```bash
|
||||
$ vim nitter.conf # Now you can edit the nitter.conf file. I won't be going into it as it is fairly straightforward.
|
||||
$ docker-compose up -d
|
||||
```
|
||||
|
||||
And voila! Now if you go to your server's IP on port 8080, you will be greeted by Nitter. Isn't that awesome?
|
||||
|
||||
Thanks to [Phin](https://filehaus.su) for helping me set it up.
|
||||
59
content/posts/running-a-fediverse-server.md
Normal file
59
content/posts/running-a-fediverse-server.md
Normal file
|
|
@ -0,0 +1,59 @@
|
|||
---
|
||||
title: "Running a fediverse server (for (nearly) free!)"
|
||||
date: 2023-07-09T09:30:00+03:00
|
||||
draft: false
|
||||
toc: true
|
||||
images:
|
||||
tags:
|
||||
- fediverse
|
||||
---
|
||||
|
||||
Running a fediverse server is now easier than ever, you can run it on hardware as low spec as a Raspberry Pi. With the recent twitter drama, it is extremely lucrative to create a fediverse account now. While you may find it easier to create an account on a more well-estabilished server, it isn't exactly the best idea. Why? Well, if you're going to make an account on a [well estabilished instance](https://joinmastodon.org/servers), you're subject to their moderation policies, and, you can get banned for some nonsensical reasons. By hosting a server, you're practically becoming censorship-resistant.
|
||||
|
||||
## Prerequisites
|
||||
* A domain name: I'd reccomend Cloudflare Domains or Porkbun.
|
||||
* A VPS: It's easy to get an Oracle Cloud Free Tier VPS.
|
||||
* Some linux experience
|
||||
|
||||
## Basic setup
|
||||
You will want to add your domain to Cloudflare, this isn't required, but it is reccomended as you may encounter bad actors trying to attack your instance. If you use Cloudflare Domains, this was already done for you.
|
||||
After you've added your domain to Cloudflare you must go to your ingress rules (instance page > vcn > subnet > security list) and add the following rules:
|
||||
```sh
|
||||
0.0.0.0/0 All Protocols All traffic for all ports
|
||||
```
|
||||
You may think that it is insecure, but we will be adding a firewall on our server now. We'll be using ufw since it is the easiest to set up for newbies.
|
||||
```sh
|
||||
sudo apt-get install ufw
|
||||
ufw allow 22
|
||||
ufw allow 80
|
||||
ufw allow 443
|
||||
```
|
||||
|
||||
## Picking your poison
|
||||
Oh well, this might be easy for some or hard for some, so I will cover each option.
|
||||
* **Mastodon**: Mastodon is the most widely-used server software on the fediverse (we're still suffering from Eugen's decisions from 7 years ago), however, it isn't the greatest. Why?
|
||||
* **Uses a lot of resources:** Mastodon is fat, which may turn you away if you want to run more than just a simple Mastodon instance on your server. Here is a comparison between Mastodon and Pleroma:
|
||||

|
||||
* **Less costumizable:** At most you can just edit the stylesheet with the default FE and add a banner. Pleroma-FE beats the fuck out of Mastodon when it comes to costumization. You can even replace Pleroma-FE with another frontend, such as soapbox.
|
||||
|
||||
If you still wish to use Mastodon, the documentation covers everything better than I could. https://docs.joinmastodon.org/admin/prerequisites/
|
||||
* **Pleroma**: Pleroma is a more sensible option if you wish to have something more light-weight. There are 3 versions:
|
||||
* **Vanilla**: The base version of Pleroma, active development has ceased unfortunately and the only updates you'll get are security fixes. (https://docs-develop.pleroma.social/backend/)
|
||||
* **Akkoma**: A fork of Pleroma that allows users to be more expressive than on Pleroma. (https://docs.akkoma.dev/)
|
||||
* **Rebased**: An improved version of Pleroma. (https://soapbox.pub/install/)
|
||||
|
||||
|
||||
All of them are trivially easy to setup and have one thing in common, the way that they are ran:
|
||||
* **From source:** you're compiling the source code every time you run the software. This opens up the posibilities of editing the source code on your server, which you may find useful in some cases. Though, depending on your server's specifications, it may take a while to run it.
|
||||
* **OTP**: OTP is the closest you can get to a binary release. It isn't compiled every time your run it, so startup times will be faster. Though, there are some limitations, most notably that you can't edit the source code
|
||||
|
||||
* **Misskey:** Misskey is by far the most feature-rich server we've covered, like Pleroma, it has many versions:
|
||||
* **Vanilla**: The base version of Misskey, without any forks. https://misskey-hub.net/en/
|
||||
* **Foundkey** [NO LONGER ACTIVELY DEVELOPED] Maintained by the same people who maintain Akkoma https://akkoma.dev/FoundKeyGang/FoundKey
|
||||
* **Firefish** [NO LONGER MAINTAINED] A more advanced version of Misskey which implements the Mastodon API https://joinfirefish.org
|
||||
|
||||
|
||||
I'd personally use Firefish as it seems more estabilished than FoundKey at this point in time. I'd reccomend any Misskey version for beginners, as it is easier to run and setup than Pleroma or Mastodon.
|
||||
|
||||
## Conclusion
|
||||
Making a fediverse server is simple, but the hard part is maintaining it.
|
||||
66
content/posts/running-a-music-server.md
Normal file
66
content/posts/running-a-music-server.md
Normal file
|
|
@ -0,0 +1,66 @@
|
|||
+++
|
||||
title = 'Running a Music Server (with Docker)'
|
||||
date = 2024-08-21T07:14:38+03:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
If you have a huge physical music collection or a desire to not pay for your music, running a Music server is a great way to organize your collection. This guide will be covering configuring [Navidrome](https://www.navidrome.org/) and [slskd](https://github.com/slskd/slskd/).
|
||||
|
||||
This tutorial will be assuming you're running your music server in the `/srv/music` directory, but it should be trivially easy for you to change where it is. We'll also be assuming you have `docker` and `docker-compose` installed.
|
||||
```bash
|
||||
# This tutorial assumes you're root
|
||||
# Firstly, we should create the /srv/music directory
|
||||
mkdir /srv/music
|
||||
cd /srv/music
|
||||
# Now we should create the compose.yml file
|
||||
nano compose.yml
|
||||
```
|
||||
**compose.yml**
|
||||
```yaml
|
||||
services:
|
||||
navidrome:
|
||||
image: deluan/navidrome:latest
|
||||
user: 1000:1000
|
||||
ports:
|
||||
- "4533:4533"
|
||||
restart: unless-stopped
|
||||
environment:
|
||||
ND_SCANSCHEDULE: 1h
|
||||
ND_LOGLEVEL: info
|
||||
ND_SESSIONTIMEOUT: 24h
|
||||
ND_BASEURL: ""
|
||||
volumes:
|
||||
- "./navidrome:/data"
|
||||
- "./soulseek/downloads:/music" # you can change this to something else if you aren't using soulseek.
|
||||
# the slskd container is entirely optional if you do not want to engage in piracy.
|
||||
slskd:
|
||||
image: slskd/slskd
|
||||
container_name: slskd
|
||||
ports:
|
||||
- "5030:5030"
|
||||
- "5031:5031"
|
||||
- "50300:50300"
|
||||
environment:
|
||||
- SLSKD_REMOTE_CONFIGURATION=true
|
||||
volumes:
|
||||
- ./soulseek:/app
|
||||
restart: always
|
||||
```
|
||||
```bash
|
||||
# Now we should run the stack to generate config files
|
||||
docker-compose up -d
|
||||
# Wait around 20-30 seconds until shutting down the containers
|
||||
docker-compose down
|
||||
# Now we'll edit the slskd config
|
||||
nano ./soulseek/slskd.yml
|
||||
```
|
||||
If you're running this locally, i.e. you won't expose this to the internet, I suggest enabling `web.authentication.disabled`. Otherwise, setup an username and a password. Don't use common usernames. Also, you must create a soulseek account and add it to your slskd config (`soulseek.username` & `soulseek.password`)
|
||||
```bash
|
||||
# Now you can run your stack
|
||||
docker-compose up -d
|
||||
```
|
||||
Now, you must configure an administrator Navidrome account. Browse to `https://[your server ip]:4533/` and make your administrator account. Now you can add your music to whatever folder you configured, or `/srv/soulseek/downloads`. For soulseek, you'll have to browse to `https://[your server ip]:5030/` and login.
|
||||
|
||||
From here, you can go bananas.
|
||||
|
||||
Thanks for reading this quick tutorial.
|
||||
78
content/posts/safely-selfhosting.md
Normal file
78
content/posts/safely-selfhosting.md
Normal file
|
|
@ -0,0 +1,78 @@
|
|||
+++
|
||||
title = 'Safely Selfhosting'
|
||||
date = 2024-09-28T12:14:03+03:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Selfhosting is a great way to fight decentralization, however, you might find yourself scratching your head as to how to expose those services to the internet. You could just port forward, but you'll have to deal with the problems of having to constantly update your home IP or having to constantly worry that some script kiddie will be able to take down your internet at home, which if you work from home, isn't very good. Thankfully, you can mitigate this issue by proxying everything through a VPS.
|
||||
|
||||
## Why should I do this?
|
||||
* You won't have to deal with dynamic DNS
|
||||
* You won't have to deal with skids taking down your internet.
|
||||
* You won't have your ISP banging at your door, demanding that you upgrade your internet service because your website is too popular.
|
||||
* You can technically run your whole setup off mobile data, but should you? No, not at all, but in case your ISP goes down you could do this.
|
||||
|
||||
## Requirements:
|
||||
* **A VPS**: ~~I reccomend https://buyvm.net/~~ ([BuyVM's future is uncertain](https://lowendtalk.com/discussion/201647/for-immediate-release-buyvm-joins-cloudzy-ai/p1)) but you can get away with most VPS providers, granted your service doesn't break their AUP. Since I am too poor to rent another VPS from them for the sake of this tutorial, I decided to use Oracle Cloud's generous free tier.
|
||||
* **A domain**: This isn't really required but realistically you're going to need one. I like https://namecheap.com/ but you could get it from other places too
|
||||
* **A server**: Duh, if you don't have one of those you'll obviously have to run your services on the VPS, which at this point, why even follow this tutorial?
|
||||
|
||||
## Step 1. setting the VPS up.
|
||||
I'll be using Ubuntu, but these commands will work on Debian too.
|
||||
```
|
||||
sudo apt install curl nginx certbot python3-certbot-nginx
|
||||
sudo systemctl enable --now nginx
|
||||
```
|
||||
|
||||
Now if we go to your VPS's IP we'll get the default nginx page.
|
||||
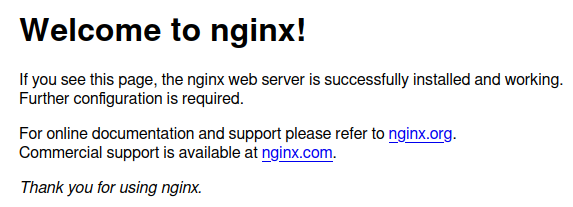
|
||||
|
||||
## Step 2. getting a VPN up and running.
|
||||
For this we'll be using OpenVPN since that's what I know best, however, you will get similar results using Wireguard if you want.
|
||||
|
||||
To make this guide as simple as possible, we'll be using [angristan/openvpn-install](https://github.com/angristan/openvpn-install), a script which automatically sets up an openvpn server.
|
||||
```
|
||||
curl -O https://raw.githubusercontent.com/angristan/openvpn-install/master/openvpn-install.sh
|
||||
chmod +x openvpn-install.sh
|
||||
sudo ./openvpn-install.sh
|
||||
```
|
||||
The setup is fairly straightforward, as such, I don't think it's necesarry I document it here. You can run the script again to add additional clients.
|
||||
|
||||
## Step 3. setting the actual server up.
|
||||
I won't go into detail on how to setup the services you want to expose to the internet.
|
||||
|
||||
First, we'll make the client connect to our OpenVPN server. You must put your .ovpn file in the /etc/openvpn/client directory, and you'll also need to change the .ovpn extension to .conf
|
||||
```
|
||||
sudo mv *.ovpn server.conf
|
||||
sudo systemctl enable --now openvpn-client@server # so we get connected on startup.
|
||||
```
|
||||
To check if you've done it correctly, you can do this:
|
||||
```
|
||||
~~curl https://fzorb.xyz/ip # this is currently broken~~
|
||||
```
|
||||
~~... and if it outputs your VPS's IP, congratulations, you've just connected your server to your VPS!~~
|
||||
You should instead check it with `ip a` and see if you have a `tun0` or similar interface for now.
|
||||
|
||||
## Step 4. forwarding HTTP requests to your own box.
|
||||
When a user wants to access your website, the Nginx server running on the VPS will reverse proxy whatever site they want to access. It's pretty simple.
|
||||
|
||||
I'll assume you know how Nginx works, so I won't go into too much detail about how to configure. Below is a pretty simple configuration which can be edited however you want. Do with it as you will.
|
||||
```conf
|
||||
server {
|
||||
server_name example;
|
||||
location / {
|
||||
proxy_pass http://10.8.0.2;
|
||||
proxy_set_header Host $host;
|
||||
proxy_set_header X-Real-IP $remote_addr;
|
||||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
|
||||
proxy_set_header X-Forwarded-Proto $scheme;
|
||||
}
|
||||
listen 80;
|
||||
listen [::]:80;
|
||||
}
|
||||
```
|
||||
|
||||
And that's not all, you can also use [Nginx TCP streams](https://docs.nginx.com/nginx/admin-guide/load-balancer/tcp-udp-load-balancer/) to forward non-HTTP services, like let's say, a Minecraft server. The possibilities are truly endless, aren't they?
|
||||
|
||||
## Step 5. profit.
|
||||
Now you've successfully exposed your service to the world wide web, isn't that cool?
|
||||
32
content/posts/t620-tc-as-a-desktop.md
Normal file
32
content/posts/t620-tc-as-a-desktop.md
Normal file
|
|
@ -0,0 +1,32 @@
|
|||
+++
|
||||
title = 'Using a 12-year-old HP T620 Thin Client as a Desktop'
|
||||
date = 2025-03-30T00:14:40+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
A few years ago, a local second hand computer store was selling T620 thin clients for dirt cheap prices, so impulsively, I bought one. From there, the humble HP T620 lived a hard life as a server for just about anything I wanted to host - git servers, forums, heck, I even once wanted to compile an Android build on it. However, there's one thing I haven't done... use it as a desktop.
|
||||
|
||||
## Why would you even want to do this?
|
||||
Science, mainly.
|
||||
|
||||
I was morbidly curious how well it would be able to cope as a remote desktop box running 24/7. It's actually kinda suited for this job, with it's low power draw, however, whenever I tried this experiment, I was running my Linux distro of choice (Linux Mint) under KVM, which led to some slight performance loss.
|
||||
|
||||
## Environment:
|
||||
- 4GB of DDR3 memory
|
||||
- Quad-Core variant (AMD GX-415TA)
|
||||
- Linux Mint 22.1 Xia
|
||||
|
||||
## General usage
|
||||
This box, while it may struggle when running multiple tabs, is actually decently usable. One of the big complaints I have though is how poorly Discord runs on it. Even then Discord is bloated garbage so whatever, it doesn't matter!!! While the animations may be sluggish, the system is decently responsive. I think I might've done a mistake by going with the Cinnamon version of Linux Mint, but it's whatever really.
|
||||
|
||||
## Gaming
|
||||
I tried a few games on it:
|
||||
- Grand Theft Auto V: got to the loading screen and then crashed (Proton)
|
||||
- Grand Theft Auto IV: Too slow to be able to even navigate the menus (Proton)
|
||||
- Half Life 2: runs at around 40-50fps on low settings
|
||||
- OpenTTD: sometimes a little sluggish
|
||||
- Minecraft: using the Fabulously Optimised modpack for 1.21.4 and with every setting turned down (including the resolution) I was averaging somewhere around 40-60fps, sometimes peaking to 100fps. Very playable. Kinda funny how this box struggled to run a Minecraft server, but can run a Minecraft client fine.
|
||||
- Towerfall Ascension: runs well, obviously.
|
||||
|
||||
## Conclusion
|
||||
Should you use this? Well, I dunno. If you can find one locally for cheap and you desperately need a computer - it probably isn't your worst option.
|
||||
22
content/posts/torchbyte.md
Normal file
22
content/posts/torchbyte.md
Normal file
|
|
@ -0,0 +1,22 @@
|
|||
+++
|
||||
title = 'Torchbyte review'
|
||||
date = 2024-11-20T21:08:00+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Torchbyte is a Romanian hosting company, with datacenters in Bucharest. Being in dire need of a cheap VPS to proxy some heavier stuff through, where lower latency would be preferred, I decided to use the aformentioned host. They're really cheap, too cheap actually, especially considering you get a dedicated IPv4 too with their EUR 4.50/quarter plan.
|
||||
|
||||
## Pros:
|
||||
* Stupidly cheap prices
|
||||
* Ability to pay with Paysafecard
|
||||
* DDoS protection (not sure how great it is though)
|
||||
|
||||
## Cons:
|
||||
* Support kinda sucks
|
||||
* You might have to go through support to do some things, because of some funny DDoS things
|
||||
* Port 25 is blocked. Support won't unblock it.
|
||||
* There have been breaches in the past. Not saying those will happen again, but I would be weary if I were you.
|
||||
|
||||
I am more than willing to look over all the cons with how cheap it is. However, the stock runs out quickly. According to Stefan over on the Discord, on the 29th of November they'll be restocking everything, so I've marked the date down, as I plan to use them with some future services.
|
||||
|
||||
If you wish to buy one, you can do so via my [affiliate link](https://billing.torchbyte.com/aff.php?aff=246) if you want to support me.
|
||||
40
content/posts/yggdrasil.md
Normal file
40
content/posts/yggdrasil.md
Normal file
|
|
@ -0,0 +1,40 @@
|
|||
+++
|
||||
title = 'Running a Yggdrasil peer on a shoestring budget'
|
||||
date = 2024-11-23T11:10:19+02:00
|
||||
draft = false
|
||||
+++
|
||||
|
||||
Recently I have been seeing this weird "Yggdrasil Network" mentioned alongside Tor and I2P. A few days ago I have started researching it, and it is really cool. Basically, it is a mesh network, but it encrypts your traffic. I think that's really cool, and while not really a privacy tool, I'd say it would be a great way to avoid any interference in your traffic by your ISP or similar.
|
||||
|
||||
So I decided that I should probably make a Yggdrasil peer. Being on a shoestring budget (as I've mentioned in the title), I decided to go with Gullo's Hosting's cheapest NAT OpenVZ VPS in Bulgaria, which should be fine, as Yggdrasil doesn't need a specific port. I also decided to go with Debian 11, because it would have a smaller footprint compared to Debian 12, and even a few megabytes would go a long way given that we have 2GB of storage... yikes!
|
||||
|
||||
## Step 0. Configure the vps properly
|
||||
I have did a mistake when initially configuring Yggdrasil: I didn't enable TUN/TAP. To be completely honest, I didn't even know that the VPS had any control panel other than the one in the billing panel. I only learnt of this when I was panicking about the fact that Yggdrasil would crash, as it couldn't find /dev/net/tun. For a bit I thought it was an issue with Gullo, but I soon learnt that it was actually an issue with me being stupid and not enabling that in the VPS' panel. Oops! Make sure to do that if you use Gullo's Hosting, like I am.
|
||||
|
||||
## Step 1. Install Yggdrasil
|
||||
The Yggdrasil documentation has a pretty good guide which you can follow [here](https://yggdrasil-network.github.io/installation.html).
|
||||
|
||||
## Step 2. Configure Yggdrasil
|
||||
This is the more tricky part. The first thing I did was get what port range I was allocated by Gullo's Hosting, which can be done easily. I then decided to peer with a bunch of peers discovered [here](https://publicpeers.neilalexander.dev/).
|
||||
|
||||
### Step 2.a Peering with others
|
||||
You have to peer with others to access the wider Yggdrasil Network. You can find peers [here](https://publicpeers.neilalexander.dev/) and you add them to your `/etc/yggdrasil/yggdrasil.conf` like so:
|
||||
```
|
||||
Peers: [
|
||||
protocol://peer:port
|
||||
]
|
||||
```
|
||||
|
||||
### Step 2.b Making your server be able to peer with others
|
||||
This is pretty simple. You just choose a random port within the range provided by Gullo and add it your config like so:
|
||||
```
|
||||
Listen: [
|
||||
tcp://0.0.0.0:port
|
||||
tls://0.0.0.0:port
|
||||
]
|
||||
```
|
||||
|
||||
## Step 3. Profit
|
||||
Now you've succesfully configured a Yggdrasil peer for just $3.50/year! Wow! To see my finished work, or to peer with me, use `tcp://bg1-ygg.kogaionon.xyz:13710` or `tls://bg1-ygg.kogaionon.xyz:13711`.
|
||||
|
||||
Also, this site is now available over Yggdrasil <a href="http://[201:acd2:6e63:671b:f32f:8a4:d7d6:3537]">here</a>!
|
||||
Loading…
Add table
Add a link
Reference in a new issue