- add back check_resetprop but rename functions to make their use more clear (thanks HuskyDG) - combine system.prop (runs at post-fs-data) entries into service.sh so that they're only set if needed (note that they therefore wouldn't need to be late props) - use a uniform style in all scripts (only necessary quoting and brackets, add trailing newlines, spaces not tabs :P) - remove GMS data pif.prop/pif.json files left over from previous releases to ensure they don't trigger detection at some point (these lines can be removed again in a later release once we're satisfied everyone affected has this resolved) |
||
|---|---|---|
| .idea | ||
| app | ||
| gradle/wrapper | ||
| module | ||
| .gitignore | ||
| .gitmodules | ||
| build.gradle.kts | ||
| changelog.md | ||
| COPYING | ||
| gradle.properties | ||
| gradlew | ||
| gradlew.bat | ||
| README.md | ||
| settings.gradle.kts | ||
| update.json | ||
| wallet-troubleshoot-1.jpg | ||
| wallet-troubleshoot-2.jpg | ||
Play Integrity Fix
A Zygisk module which fixes "ctsProfileMatch" (SafetyNet) and "MEETS_DEVICE_INTEGRITY" (Play Integrity).
To use this module you must have one of the following:
- Magisk with Zygisk enabled.
- KernelSU with ZygiskNext module installed.
Telegram group
Donations
Official posts
About module
It injects a classes.dex file to modify a few fields in the android.os.Build class. Also, it creates a hook in the native code to modify system properties. These are spoofed only to Google Play Services' DroidGuard (SafetyNet/Play Integrity) service.
The purpose of the module is to avoid a hardware attestation.
About 'pif.json' file
You can modify this file in the module directory to spoof custom values to the GMS unstable process.
You can't use values from recent devices due them triggering hardware backed attestation.
Troubleshooting
Failing BASIC verdict
If you are failing basicIntegrity (SafetyNet) or MEETS_BASIC_INTEGRITY (Play Integrity) something is wrong in your setup. Recommended steps in order to find the problem:
- Disable all modules except this one
Some modules which modify system can trigger DroidGuard detection, never hook GMS processes.
Failing DEVICE verdict (on KernelSU)
- Disable ZygiskNext
- Reboot
- Enable ZygiskNext
Play Protect/Store Certification and Google Wallet Tap To Pay Setup Security Requirements
Follow these steps:
- Flash the module in Magisk/KernelSU
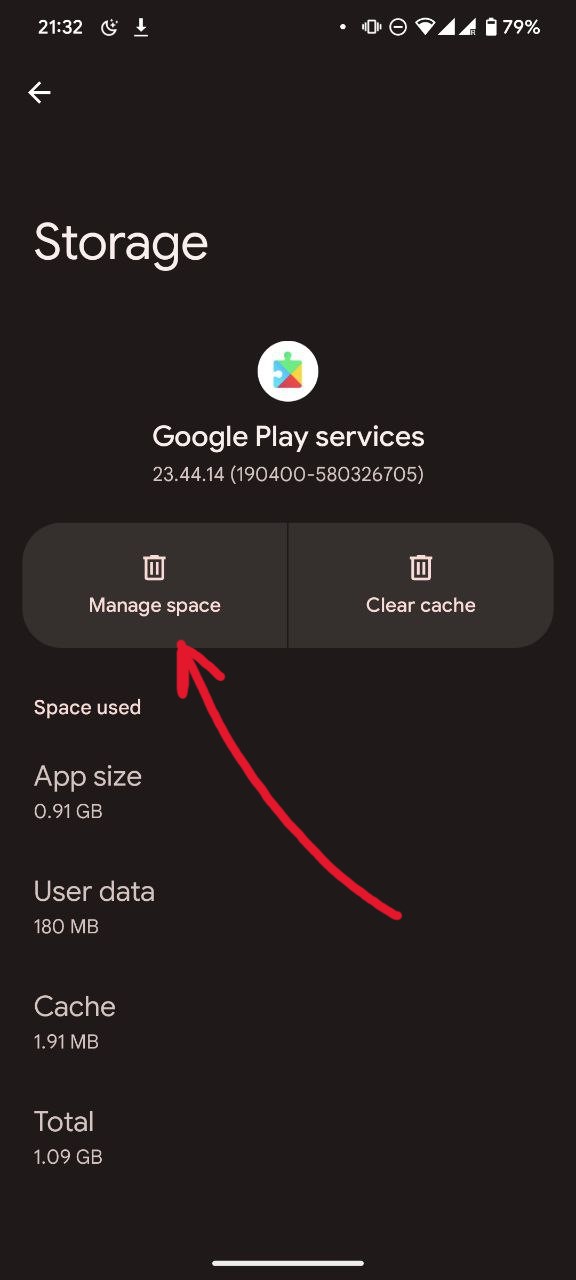
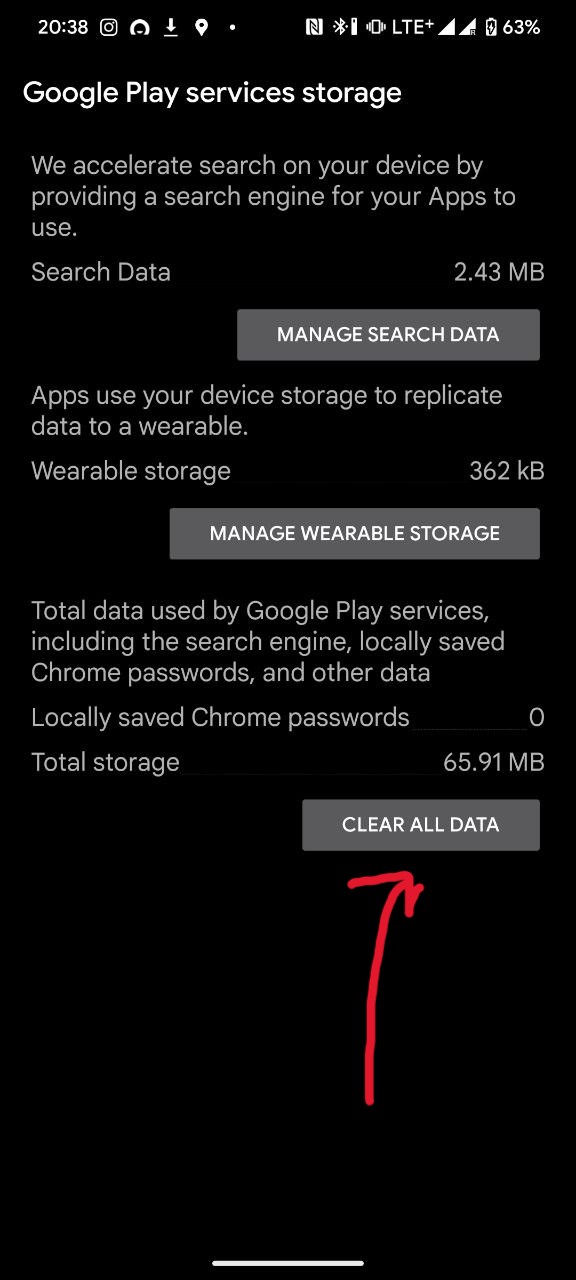
- Clear Google Wallet cache (if you have it)
- Clear Google Play Store cache and data
- Clear Google Play Services (com.google.android.gms) cache and data (Optionally skip clearing data and wait some time, ~24h, for it to resolve on its own)
- Reboot
Read module logs
You can read module logs using this command directly after boot:
adb shell "logcat | grep 'PIF'"
Can this module pass MEETS_STRONG_INTEGRITY?
No.
About Play Integrity, SafetyNet is deprecated
You can read more info here: click me